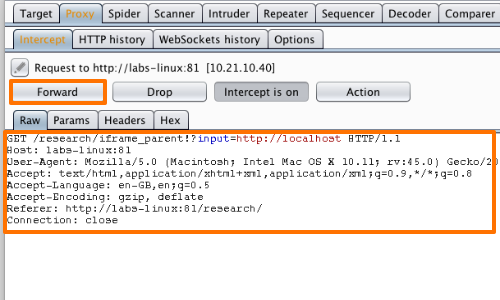
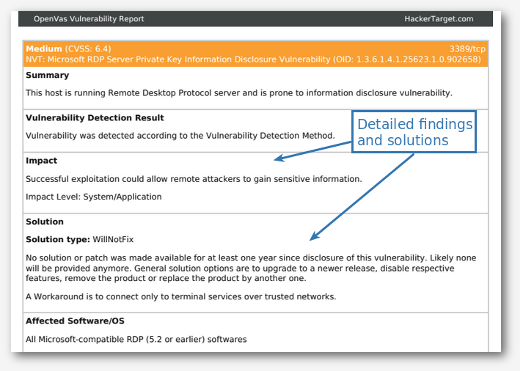
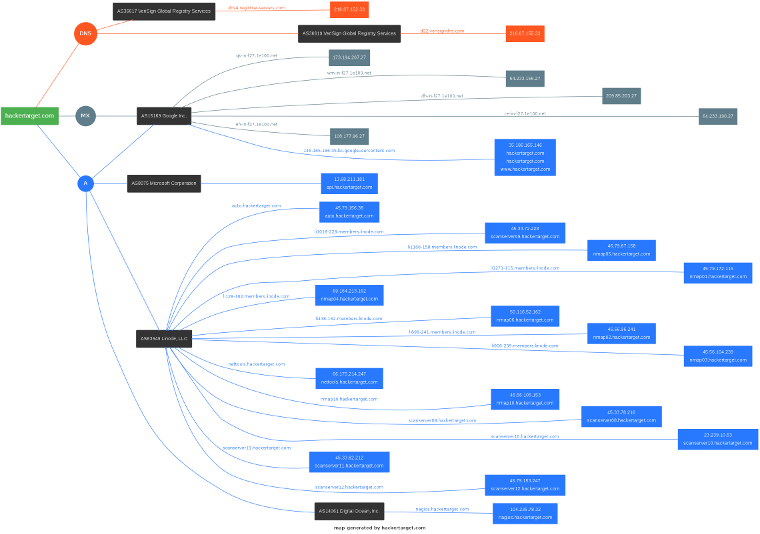
A vulnerability scanner is a software tool that can detect vulnerabilities and weaknesses within a network, system, or application. Although the concept may seem straightforward, the process itself is more complex.
For most organisations, having a thorough understanding of assets and conducting regular vulnerability scanning is the most cost-effective approach to getting security under control.
Once vulnerabilities are detected, it's time to evaluate and assess the risk. This allows you to priortise and work on mitigation (a fancy way of saying reduce the assessed risk).
With the big budget spending around cyber security, the humble vulnerability scanner can be passed over for buzzwords like threat intelligence, red teams, security analytics, threat hunting, and even penetration testing. All these technologies and processes have their place within a security strategy, but without a clear understanding of vulnerability exposure and potential attack surface, these can become a distraction.