Easy approvals as there is zero impact on your network.
Attack Surface Assessment
THE ATTACKERS PERSPECTIVE
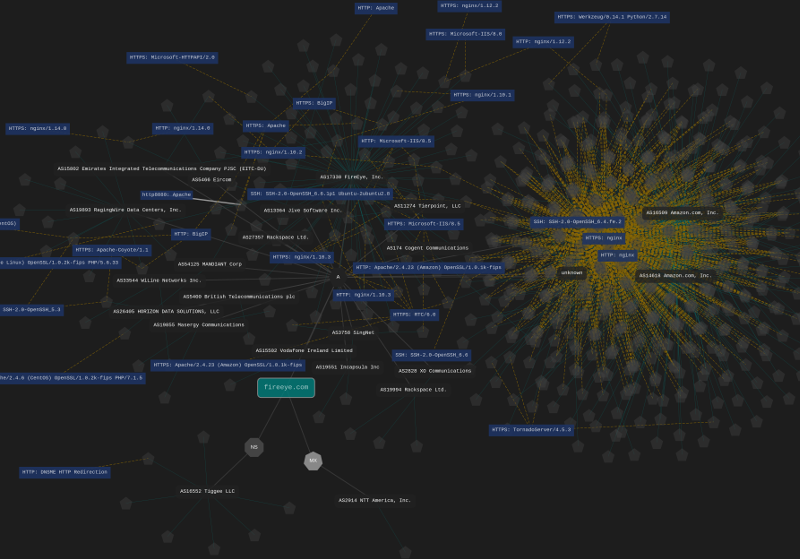
Using open source intelligence (OSINT) we map your organisations network and compile a detailed report. By using Internet Wide Scan Data we have zero impact on your network.
- Zero Impact on Target
- Fixed price assessment
- Fast turn around (72 hrs)
- Clear results from the attackers perspective
- Compare results with Asset Register
- Custom Options Available
- Attack Surface Analysis x4 (Quarterly)
- Hassle Free Regular Assessments
- Monitor Ongoing System Changes
- Clear results from the attackers perspective
- Compare results with Asset Register
- Custom Options Available
Some Common Questions
The target of this assessment is network resources, systems and endpoints. There is no targeting of organisations members or employees for social engineering purposes.

The report will be delivered as a PDF and a Spreadsheet and contain:
- Discovered Host names
- Discovered IP addresses and Network Blocks
- Discovered open services (from Internet wide Scan Data not active port scans)
- Email addresses found in breach data sets, including details on breach and information compromised
- Metadata from documents, code leaks, S3 Buckets and other information leaks relevant to the organisation
- Related Security & Network Information sourced from open source (OSINT)
Another third party assessment we offer is a focused External Vulnerability Assessment. This involves active vulnerability scanning and validation of the detected vulnerabilities.
Sample Resources used:
- HackerTarget.com IP Tools
- CommonCrawl Website Archive
- Certificate Transparency Logs
- Reverse Whois searches for related domains
- Shodan.io and other Internet Wide Scanners
- Pastebin and other resources used by threat groups
- Search Engines (Google Dorks)
- Twitter / Facebook / Github and other Social Media Platforms
- Metadata leaks in published resources
- Other custom resources and data sets as required
Rest assured that our focus does not impact our availability to answer your questions before, during and after the assessment.
Get Started Here
Complete this form to request an Attack Surface Assessment of your Internet facing systems. We will get back to you within 24 hours with a proposed plan, terms of the service and payment details.
If there are particular systems or networks you would like the assessment to focus on then please detail these requirements. In this case a high level security assessment will be conducted against the target, with focused testing performed against the system or network of particular interest.
With this fixed rate security assessment testing is conducted in a 48 hour window, with report delivered within 72 hours.
- You must be the owner of the system or have explicit permission to have a third party security assessment performed against the target organisation.
- An understanding that while we are primarily relying on open source information sources, there is a chance that some requests may access the organisations systems. For example, DNS requests against discovered systems.
Deliverables:
- Detailed Security Report delivered within 72 hours.
- Report to contain discovered results and recommended remediation.
- Follow up questions to be conducted via email.