These use cases scratch the surface of what is possible.
Know the Network.
Know the Attack Surface.
With a bundle of 28 different vulnerability scanners and network tools, you will find solutions for a wide range of problems.
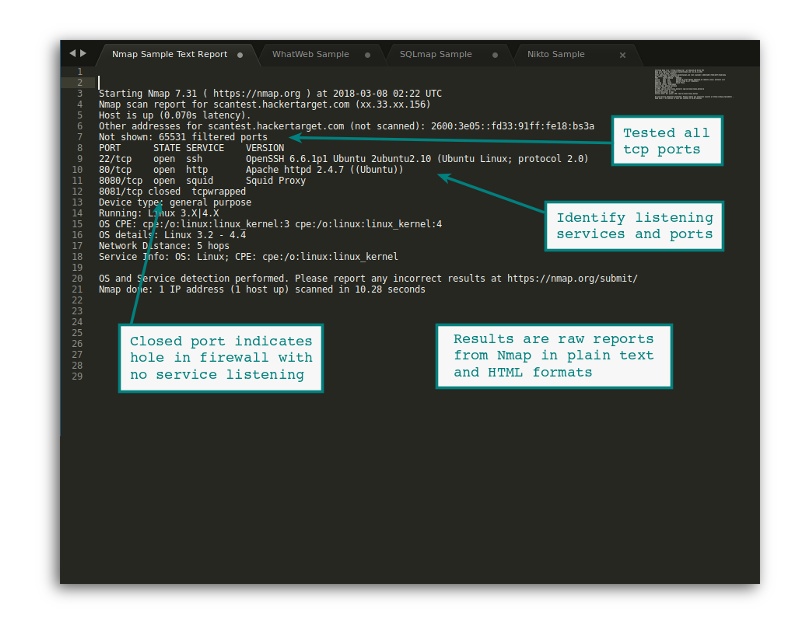
Nmap Port Scanner
Firewall Monitoring
Schedule Nmap to monitor Internet facing services on a host, network or entire ASN.
DevOps Network Visibility
From troubleshooting network services to checking open ports on rapidly deployed systems.
Detect Human Error
System Administration is sometimes like drinking from a fire hose. Mistakes happen, with Nmap quickly discover services that should not be on the Internet.
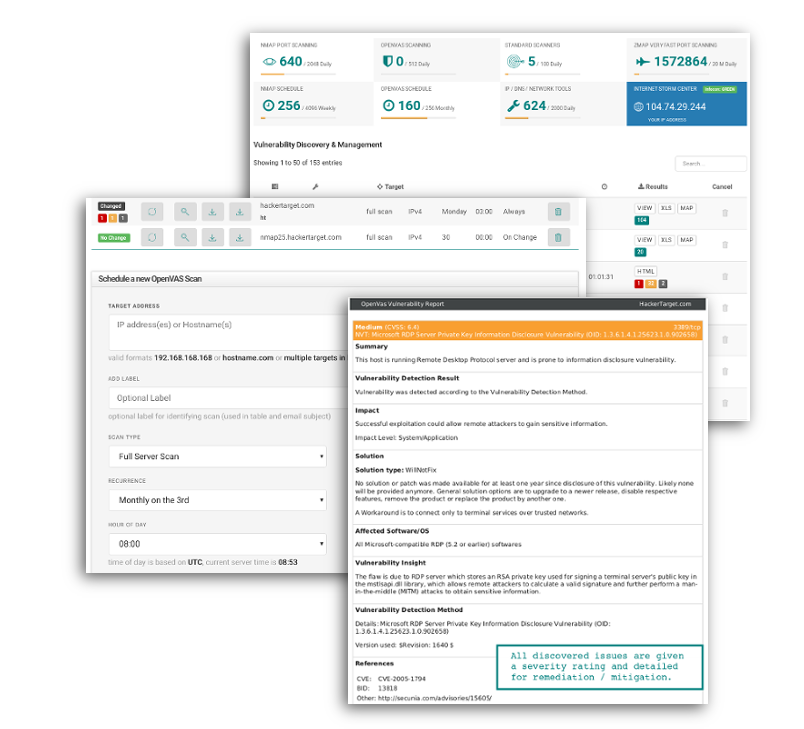
OpenVAS Vulnerability Scanner
Comprehensive Vulnerability Discovery
Detect a wide range of network service and web application vulnerabilities across any Internet facing system.
Ongoing Vulnerability Management
Schedule scans for weekly or monthly reports. Configure report to alert on changes to vulnerability count.
Real Time Risk Visibility
Detailed reports that include vulnerability severity with technical details of immediate value to the user.
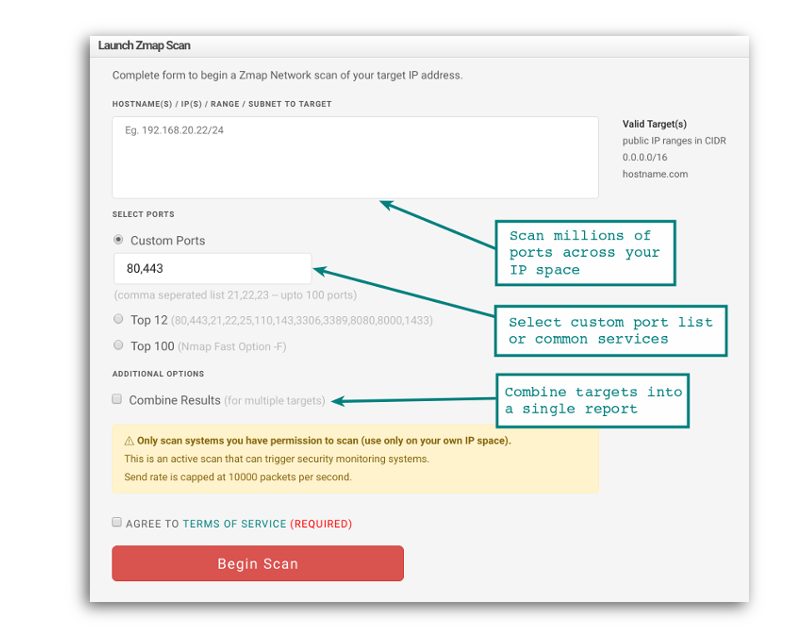
Zmap = Wide Scope Scanning
Enterprise Wide Port Scans
Enterprises with large amounts of IP space will benefit from fast scans of hundreds of thousands of IP addresses.
Know Your Exposure
When a new threat hits the cyber news feed; fire off a scan and get real time visibility across your entire address space.
Attack Surface Mapping
Get an accurate picture of your attack surface in a few minutes. Discover RDP, SSH, VPN Endpoints and more across your external infrastructure.
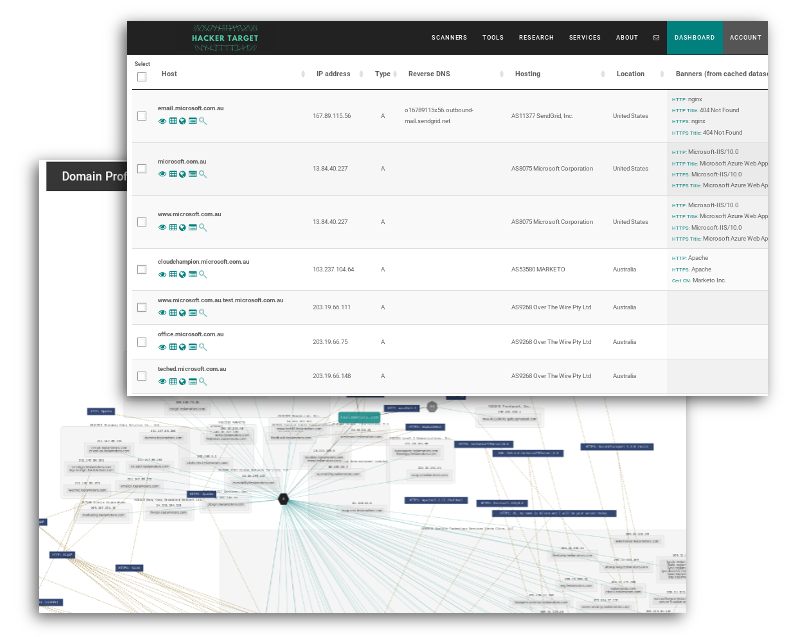
Recon with Domain Profiler
Enterprise Wide Discovery
Identify endpoints across an entire organization using DNS data sets and Internet wide scan data.
Shadow IT Infrastructure
Teams change, staff leave and systems are forgotten. Find unmanaged, unpatched systems that are still accessible from the Internet.
Asset Discovery Against Any Domain
Get an overview of any targets Internet Infrastructure. Research competitors. Win Bug Bounties. Red Teams and Penetration Tests. Game On.
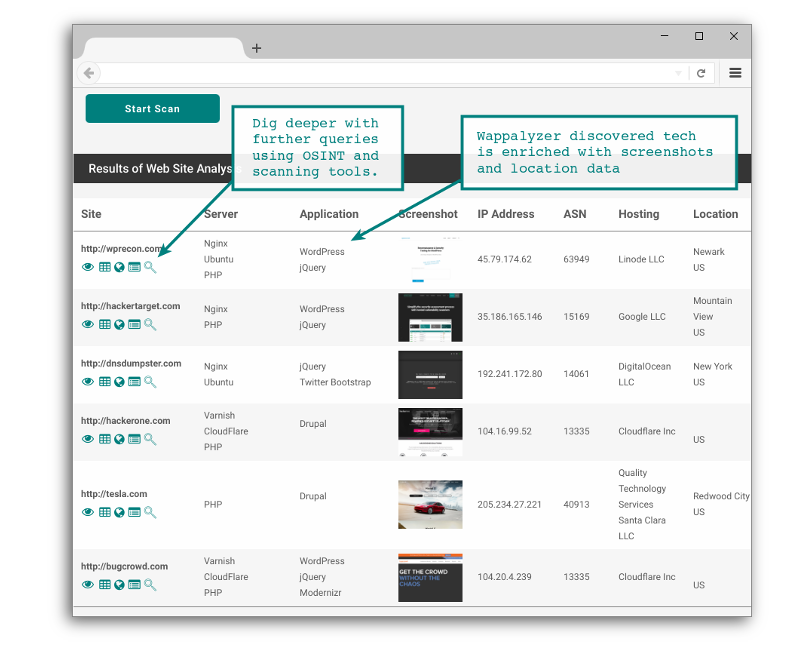
Tactical Web Analysis
Investigate Web Endpoints
Determine web technologies in use on both front end and server side. Gather screenshots for at a glance review.
Bulk Analysis
Paste a list of web sites or host names and get an overview of any HTTP based services. Test up to 1000 sites at time.
Low Impact Research
Analysis is performed from a simple HTTP GET request. Low Impact. Use for Bug Bounties, Pentests and other Internet Research.
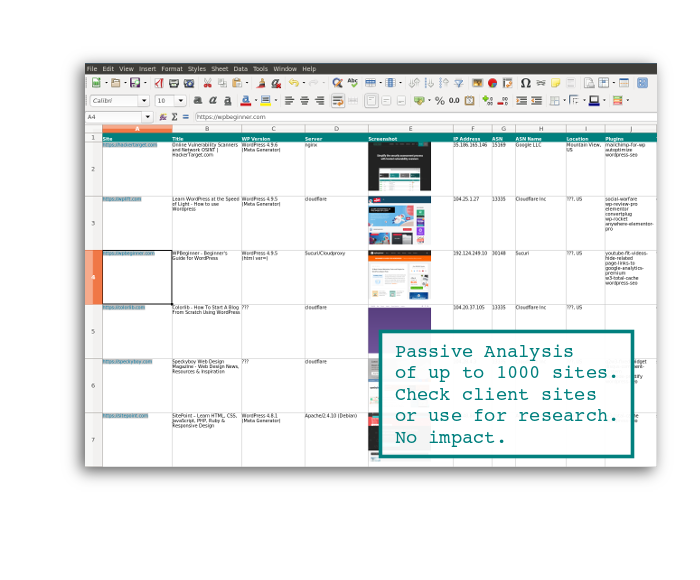
Focused WordPress Review
At a glance Security Review
Identify WordPress Core Version, plugins and more across a list of WordPress based properties.
WordPress Agencies
Review customer site status, prospective customers and internal sites in bulk. No impact.
Hunting for Weak Spots
Penetration Testers, Bug Bounty Hunters and Security Analysts can quickly review large numbers of sites to find those that may not be well managed.
HUNT
Hunt vulnerabilities across your Internet facing assets.
PROTECT
Protect your endpoints with improved visibility. Know your network.
DISCOVER
Discover Internet facing assets for any target organization.
RESEARCH
Network research tools for DFIR, Threat Hunting & Operations.
Test IN BULK
Paste lists of targets into the scanning tools for bulk analysis.
SIMPLY LAUNCH
Simple form to launch tests. Results available in email or dashboard.
ALWAYS ON
Scanning infrastructure ready to go whenever you are. Test anytime.
CUSTOM REPORTS
Reports contain raw tactical output. Paste into custom reports.