OpenVAS Vulnerability Scan
The OpenVAS scanner is a comprehensive vulnerability assessment system that can detect security issues in all manner of servers and network devices. Use this hosted version of the OpenVAS software to effortlessly test your Internet infrastructure.
Results are delivered to your email address for analysis, allowing you to start re-mediating any risks your systems face from external threats.
Detect vulnerabilities in servers, networks and web sites
- Find security vulnerabilities in any Internet facing system
- Detailed reporting for risk assessment and re-mediation
- Vulnerability Alerts on detected change in scheduled report
- Custom scan options; Network/Server, Web, WordPress and Joomla Scans
- Access to 27 Vulnerability Scanners and OSINT Tools
- Trusted Open Source Tools
Why would I use the OpenVAS scanner?
The primary reason to use this scan type is to perform comprehensive security testing of an IP address. It will initially conduct a port scan of an IP address to find open services. Once listening services are discovered, they are tested for known vulnerabilities and misconfiguration using a large database (more than 53000 NVT checks). The results are compiled into a report, including detailed information regarding each vulnerability and notable issues discovered.
Once you receive the results of the tests, you will need to check each finding for relevance and possibly false positives. Any confirmed vulnerabilities should be re-mediated to ensure your systems are not at risk.
Vulnerability scans performed from externally hosted servers give you the same perspective as an attacker. This has the advantage of understanding exactly what is exposed on external facing services.
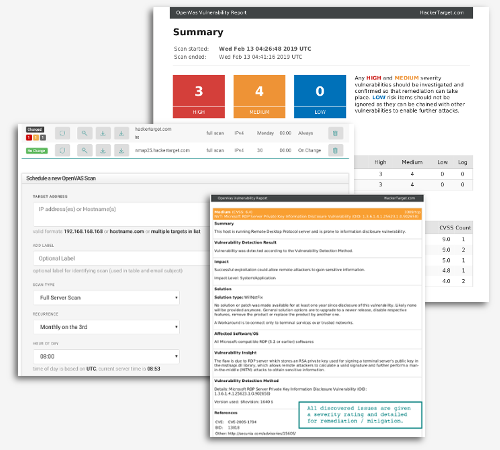
Sample OpenVAS Reports
How does the hosted OpenVAS process work?
1. Enter the target to scan
Depending on your goals and the target being tested; enter an IP address, a range of IP addresses (PRO membership required) or hostname. Different targets can be entered as a list to run as separate jobs or as a single job for a consolidated report.
- Target host name will be resolved to all its IPv4 and IPv6 addresses for testing.
- No hosts found? Blocking ICMP? It is recommended to allow ICMP from our servers so that host discovery is successful. If
icmp (ping)is blocked the following TCP ports will be tested to determine if the host is alive (21,22,23,25,53,80,110,111,135,139,143,443,445,993,995,1723,3306,3389,5900,8080,137,587,3128,8081).
2. Select scan type
Multiple options are available depending on the type of system to be tested.
Full Scan for a full test of network, server and web application vulnerabilities.
Web Server Scan a more focused test for web server and web application vulnerabilities (ports 80 and 443 only).
WordPress Scan testing for known WordPress vulnerabilities and web server issues (ports 80 and 443 only).
Joomla Scan testing for known Joomla vulnerabilities and web server issues (ports 80 and 443 only).
3. Launch the Vulnerability Scan!
Testing will begin and the target system(s) will be probed in order to discover vulnerabilities that could place the system at risk of compromise. Results will be available from 15 minutes to a number of hours depending on the target selection.
See our overview for more on detection and mitigation of Log4j.
Technical details of the scan configuration
A number of high performance servers are hosting OpenVAS/GVM 21.4. The NVT's or vulnerability database is updated multiple times a week or as required, using the open source signature feed (community feed). For Enterprise Software Vulnerability testing and internal network scanning we recommend looking at the Greenbone Security Manager range of appliances. Combine an Internal appliance with our external facing suite of tools for full coverage of across all your network attack surface.
OpenVAS / GVM is configured to run using configurations based off the "Full and Fast Scan" profile. Hosts are found to be alive after testing for an ICMP response or if this fails a test against common TCP ports. If no open ports are found and ICMP is blocked the target will be seen as not responding and a full scan will not be performed.
ICMP with no common TCP ports open or it is behind an Intrusion Prevention System / Firewall that has blocked the scanners source IP address after detecting the scan.Vulnerability Testing from behind a firewall or intrusion prevention device is generally unreliable - timeouts, slow scanning (rate limiting) and differences in the results can sometimes be observed. We balance the need for testing as many targets as possible with the performance requirements of Internet based scanning.
We have observed that testing of CloudFlare based sites and some systems behind web application firewalls or intrusion protection systems can be unreliable and likely slow. This is due to rate limiting and blocking offered by the WAF / security application.
The options for a Web Server focused scan and the Content Management Scans are configured for testing sites on ports 80 and 443 only. We also have our standalone Nikto security scanner available for a focused web server scan.
 "Continuously acquire, assess, and take action on new information in order to identify vulnerabilities, remediate, and minimize the window of opportunity for attackers."
"Continuously acquire, assess, and take action on new information in order to identify vulnerabilities, remediate, and minimize the window of opportunity for attackers."
About the OpenVAS project
 OpenVas / GVM is an open source vulnerability scanner that can test a system for security holes using a database of over 95’0000 NVT test plugins. This covers more than 185000 CVE's. The complete OpenVAS suite consists of a number of components that provide a framework for management of a complete vulnerability management solution.
OpenVas / GVM is an open source vulnerability scanner that can test a system for security holes using a database of over 95’0000 NVT test plugins. This covers more than 185000 CVE's. The complete OpenVAS suite consists of a number of components that provide a framework for management of a complete vulnerability management solution.
Whether you are using the standalone tool or the service we offer here OpenVAS is a excellent way to test an Internet connected server, firewall and listening services for configuration errors and known vulnerabilities.
Commercial Security Scanning Solutions
Depending on your needs and your budget there are a number of different well known vulnerability scanners available. A number of years ago I did a comparison of OpenVAS against other leading solutions. My conclusion was that no single solution will provide 100% coverage.
For those with the budget running OpenVAS alongside a commercial vulnerability scanner can be an excellent way to validate results and get a more accurate picture. Comparing results from two or more different solutions can reveal false positives and false negatives.
Best practice vulnerability scanning requires that you utilize multiple tools. This is similar to email threat mitigation using multiple solutions (an email filtering gateway and a local end point anti-virus product that use different scan engines). While you may use a commercial vulnerability scanner or service such as Greenbone Security Manager, Nessus, Nexpose or GFI Languard; having a hosted version of OpenVAS available is excellent way to get a second set of results for a public Internet facing service.
One of the advantages of OpenVAS being open source, is that when you receive a false positive; you are able to review the plugin to determine why the vulnerability was flagged. OpenVAS has a strong community of security practitioners and posting any false positive to the OpenVAS mailing list often results in immediate feedback. This can result in the false positive being fixed within hours to the benefit of the whole community.